When setting up Active Directory delegation, you want administrators to be able to maintain Group Policy without being a Domain Admin. If you read TechNet, Microsoft tells you to use Group Policy Creator Owners, please see:
http://technet.microsoft.com/en-us/library/cc776858.aspx
Lets test it. We have a user named Jess. Jess is only a member of the domain users group. We add Jess to “Group Policy Creator Owners”. Jess creates a group policy object called “Jess’s Policy”. Great, it worked. If we look at the permissions of “Jess’s Policy” in group policy management console (GPMC), we see that she has permissions to the group policy object.
Jess does not have permissions to modify or edit any other group policy objects.
The problem with Group Policy Creator Owners
Lets say you have 10 administrators that need to make group policy changes. You add the 10 administrators to Group Policy Creator Owners. One administrator creates a group policy object. The others cannot read or modify the group policy object as only the administrator that created the group policy object owns it. The administrator that created the group policy object must remember to grant the other administrators access to the group policy object. This process needs to re-occur every time an administrator creates a new group policy object.
I don’t know why Microsoft recommends to use this approach for group policy delegation as it is not feasible.
The Solution
Change the template permissions in Active Directory!
By default whenever you create a new GPO the following Active Directory system groups are granted access:
– Authenticated Users
– Domain Admins
– Enterprise Admins
– ENTERPRISE DOMAIN CONTROLLERS
– SYSTEM
These permissions are the “default” permission template for newly created group policy objects. We can add additional custom groups to this template by modifying the Active Directory Schema Partition.
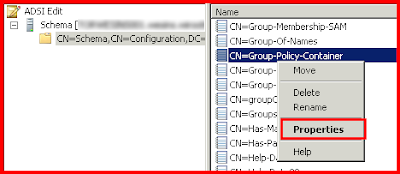
To do this use ADSIEdit and connect to the Schema Partition.
View the properties for CN=Group-Policy-Contrainer
The defaultSecurityDescriptor attribute contains the security template for all new group policy objects. By default the defaultSecurityDescriptor looks like this:
D:P(A;CI;RPWPCCDCLCLOLORCWOWDSDDTSW;;;DA)(A;CI;RPWPCCDCLCLOLORCWOWDSDDTSW;;;EA)(A;CI;RPWPCCDCLCLOLORCWOWDSDDTSW;;;CO)(A;CI;RPWPCCDCLCLORCWOWDSDDTSW;;;SY)(A;CI;RPLCLORC;;;AU)(OA;CI;CR;edacfd8f-ffb3-11d1-b41d-00a0c968f939;;AU)(A;CI;LCRPLORC;;;ED)
Schema permissions are written by using the Security Descriptor Definition Language (SDDL).
Note: These SID’s will be different in your environment as the beginning of a SID is unique to the given domain.
The beginning of each ACL states what permissions are set over the group or username entry. The second part shows the SID of the group/user account.
I have created a group called AD-GPO-M that I want to add to the template permissions to ensure they get applied to all new group policy objects. We added the following to the end of my SDDL on the defaultSecurityDescriptor attribute. This is the SID that is append to the AD-GPO-M security group.
(A;CI;RPWPCCDCLCLOLORCWOWDSDDTSW;;;S-1-5-21-1445357118-337764505-1417137283-24392)
On the CN=Group-Policy-Contrainer Active Directory object, the defaultSecurityDescriptor attribute now reads:
D:P(A;CI;RPWPCCDCLCLOLORCWOWDSDDTSW;;;DA)(A;CI;RPWPCCDCLCLOLORCWOWDSDDTSW;;;EA)(A;CI;RPWPCCDCLCLOLORCWOWDSDDTSW;;;CO)(A;CI;RPWPCCDCLCLORCWOWDSDDTSW;;;SY)(A;CI;RPLCLORC;;;AU)(OA;CI;CR;edacfd8f-ffb3-11d1-b41d-00a0c968f939;;AU)(A;CI;LCRPLORC;;;ED)(A;CI;RPWPCCDCLCLOLORCWOWDSDDTSW;;;S-1-5-21-1445357118-337764505-1417137283-24392)
Now when I created a new group policy object (GPO) called “Test PCI Member Server” the following permissions were granted by default:
This has now given your non-domain admins who are a member of this group permissions to administer this new group policy object.
For any existing group policy objects they will not currently have access, however you can reset permissions to default which will pull the permissions down from the defaultSecurityDescriptor attribute.
Where are these permissions set?
Permissions for your group policy objects are maintained in two locations.
– Active Directory
– SYSVOL policies container
Whenever you make a change to permissions on a group policy object in group policy management console (GPMC) it will modify permissions on both the Active Directory object and SYSVOL.
In Active Directory the group policy objects are stored under your domain partition –> System –> Policies.
Caution for Multi-Domain Forest
In a multi-domain forest, your administrator account may reside in a Child Domain. You may be nested in the Schema Admins group in the forest root domain. When you use ADSIEdit to modify the CN=Group-Policy-Contrainer on the schema partition you may receive the following error:
Operation failed. Error code: 0x202b
A referral was returned from the server.
0000202B: RefErr: DSID-030A0B09, data 0, 1 access points
ref 1:
I found you need to connect to the schema master in your forest root domain to make this change in ADSIEdit. This resolved the problem.
You may also want to read the Knowledge Base article about this, you can also find more information about Security Descriptor String Format.
Also thanks clintboessen for the original post.






To add Full admin permissions:
(A;CI;RPWPCCDCLCLOLORCWOWDSDDTSW;;;SID)
If you want to add Read-only as default permission:
(A;CI;LCRPLORC;;;SID)